What’s up, everyone!
Did you catch the latest episode of Windows in the Cloud? In this episode Christiaan Brinkhoff and legends of the product team announced a couple of great things! One of them being that Windows 365 Frontline now supports Windows 365 Boot! To me this is just on those things that makes absolute sense! This allows organizations to configure their endpoints with Windows 365 Boot so users can directly sign into their Cloud PC. Now combine this with a Frontline type of license where users will typically work in shifts or different endpoints during their shift and you can already see the magic happen.
You guessed it, welcome to the post where we will combine Windows 365 Boot with Windows 365 Frontline!
Requirements
These are the requirements if you want to follow along;
- A Microsoft tenant
- Intune administrator role / Windows 365 administrator or global admin
- A Windows 365 Frontline license
- Users must be licenses for Windows 10/11 Enterprise, Microsoft Intune and Entra ID P1. Since these are already included in M365 E3, E5 etc, chances are that your users are already licensed accordingly.
- Windows 365 Boot works on a VM 🙂
Configuring Windows 365 Frontline
We can focus on setting up Windows 365 Frontline now that we got the requirements out of the way. Windows 365 Frontline is now GA and I do wonder if anything changed while it was in public preview, like when I wrote an introduction about Windows 365 Frontline.
I’ve started by creating a couple of demo users in my tenant and I’ve assigned Microsoft 365 E3 licenses to them. All that’s left to do is create a provisioning policy and we should be good to go!
From the Microsoft Intune admin center, go to Devices, Windows 365, Provisioning Policies. Click the + Create policy button in the ribbon.
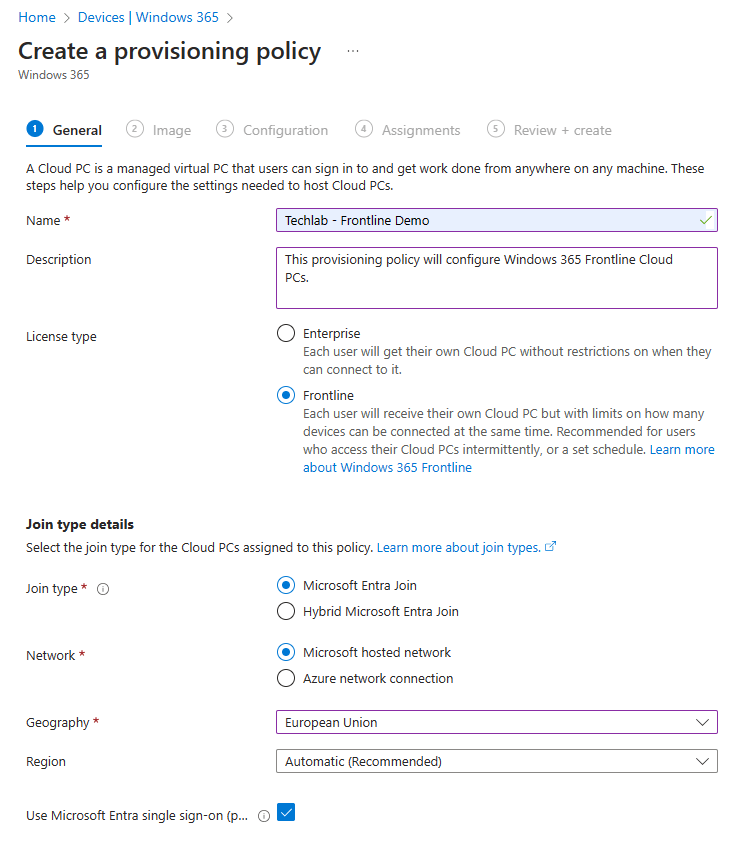
Give the provisioning policy a name and make sure to check the Frontline license type. In my demo environment I’m all good with a Cloud PC that’s Microsoft Entra joined and lives on a Microsoft hosted network. Only thing that’s left is to choose the geography and region that works for you. Enabling SSO will improve the user experience so I’m a huge fan of that. I ended up with something like this;
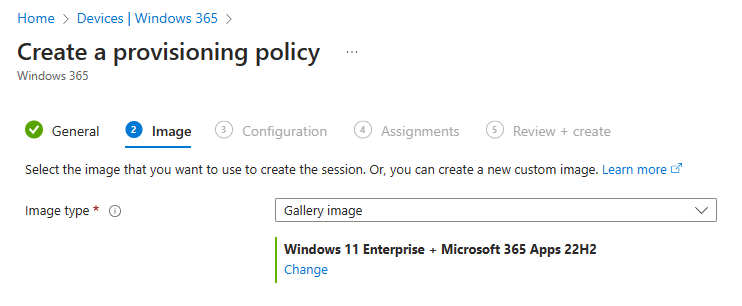
Using the default latest and greatest Windows 11 image with the M365 Apps is perfect for this demo.
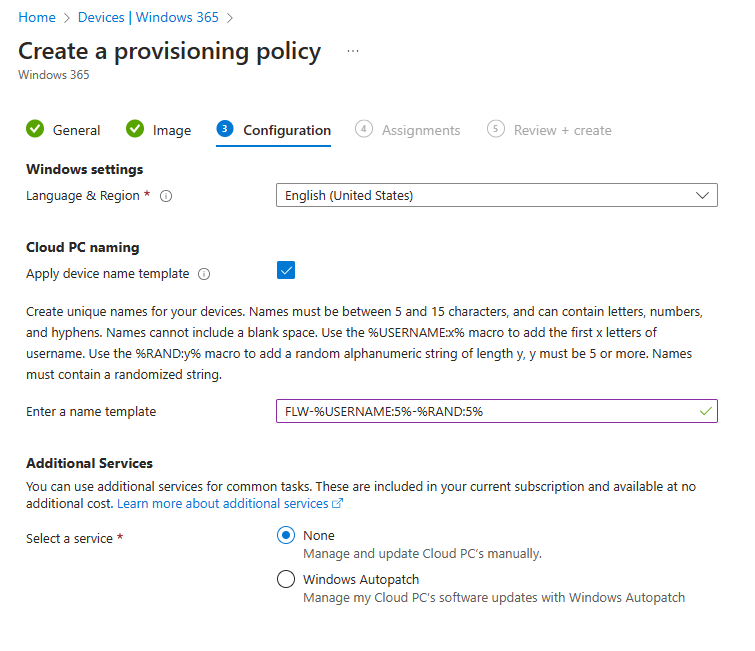
In the Configuration tab we can choose the language and region settings, apply a Cloud PC naming template and enable Windows Autopatch if you have that up-and-running in your tenant.
I currently not using Windows Autopatch in my tenant so I’ll leave that unchecked. But I like to see if a Cloud PC is an Enterprise Cloud PC or a Frontline Cloud PC. So configuring a naming template makes sense.
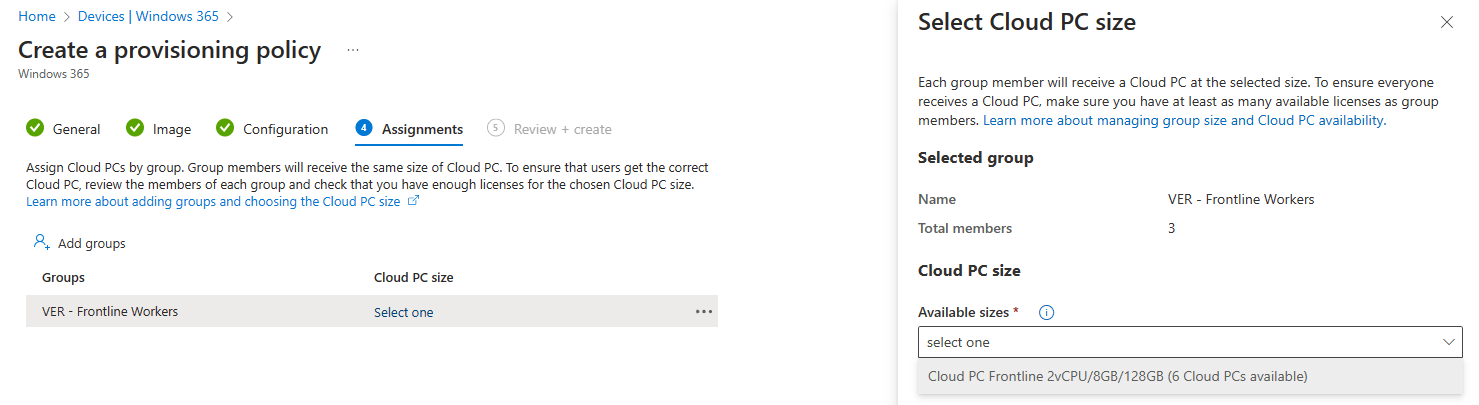
Now it’s time to assign the provisioning policy to a group of users. I’ve already created a group and added my Fronline workers to it. Click the Select one text in the Cloud PC size to get access to a tab where you can select the Frontline license.
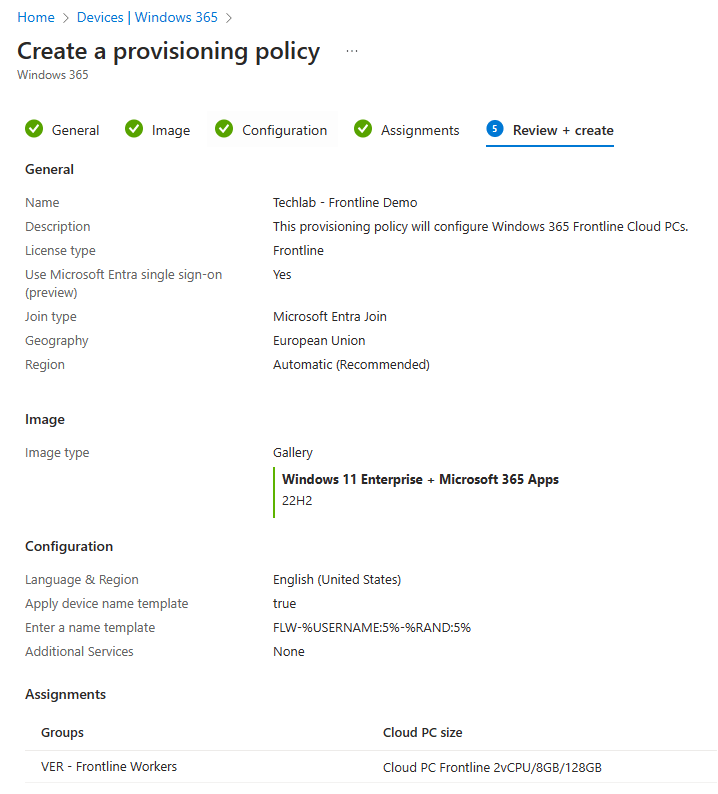
The only thing that’s left to do is to admire your awesome work and create the policy if you are happy with it.
Configuring Windows 365 Boot
I wrote an introduction into Windows 365 Boot earlier this year. It’s still a relevant post as it goes into more detail on how to configure this feature and the requirements.
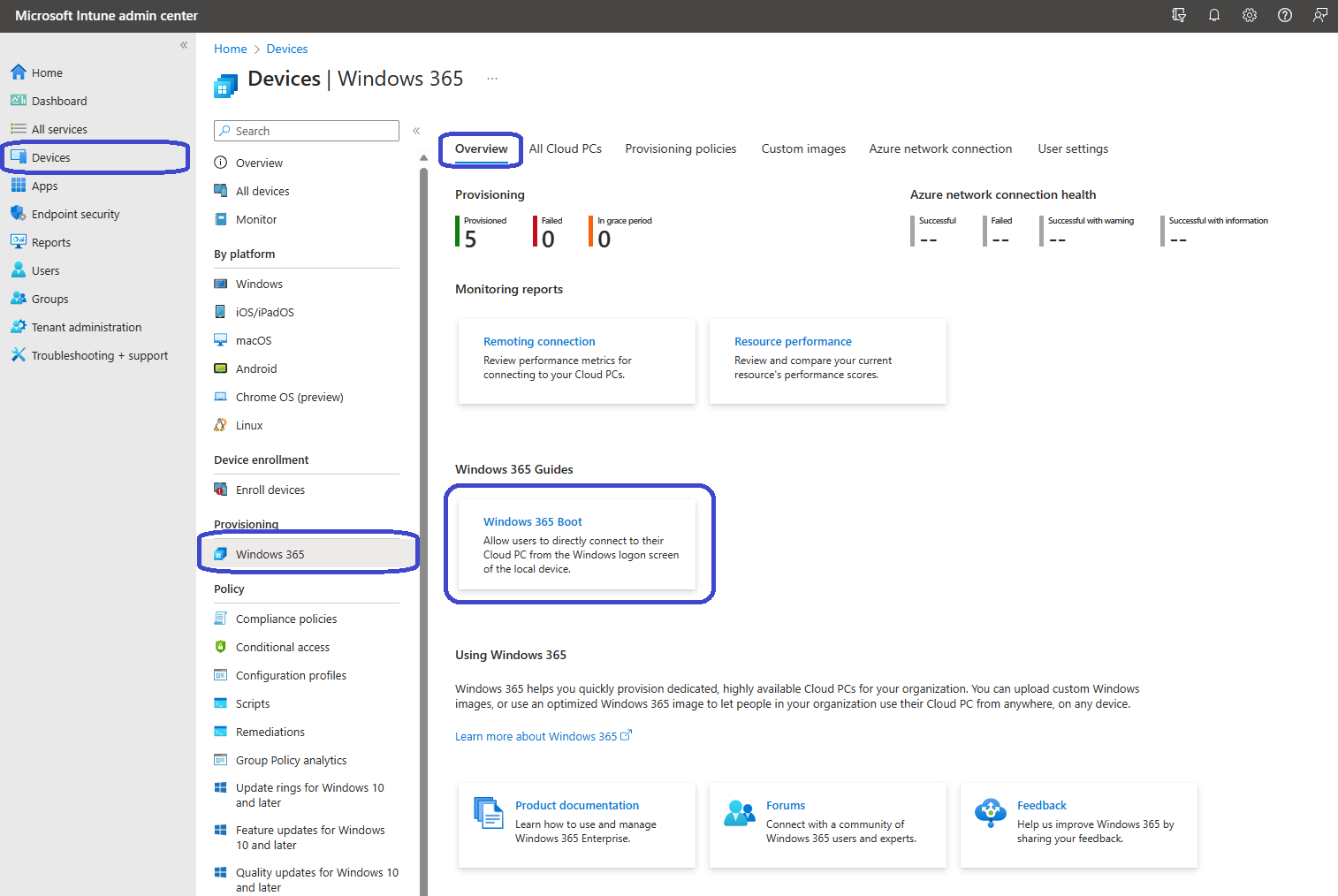
We can configure Windows 365 Boot using a Windows 365 Boot guide. You can find it in Microsoft Intune admin center, Devices, Windows 365, Overview, Windows 365 Guides.
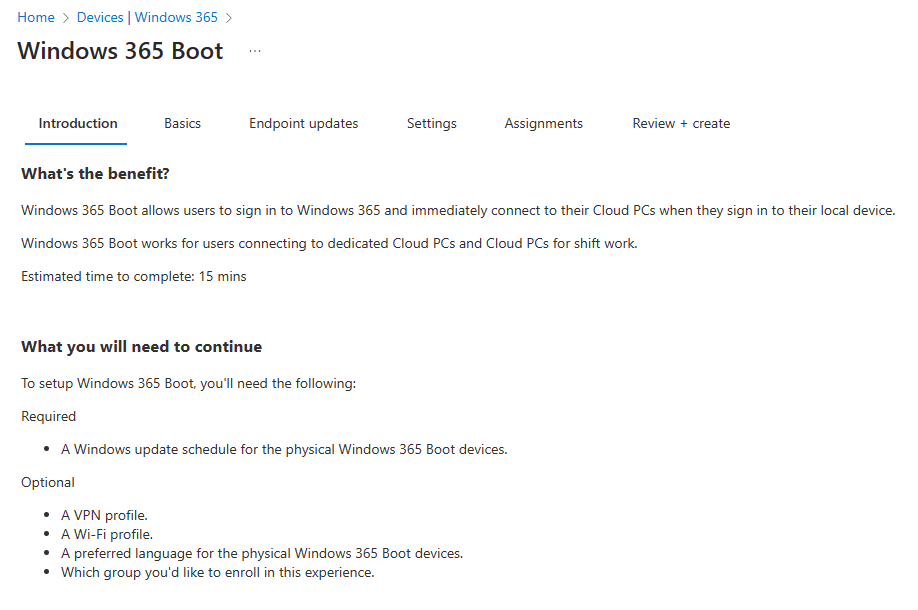
The introduction section will give you an idea of the things that we are about to configure.
The only requirement is that we need to have an update schedule in place.
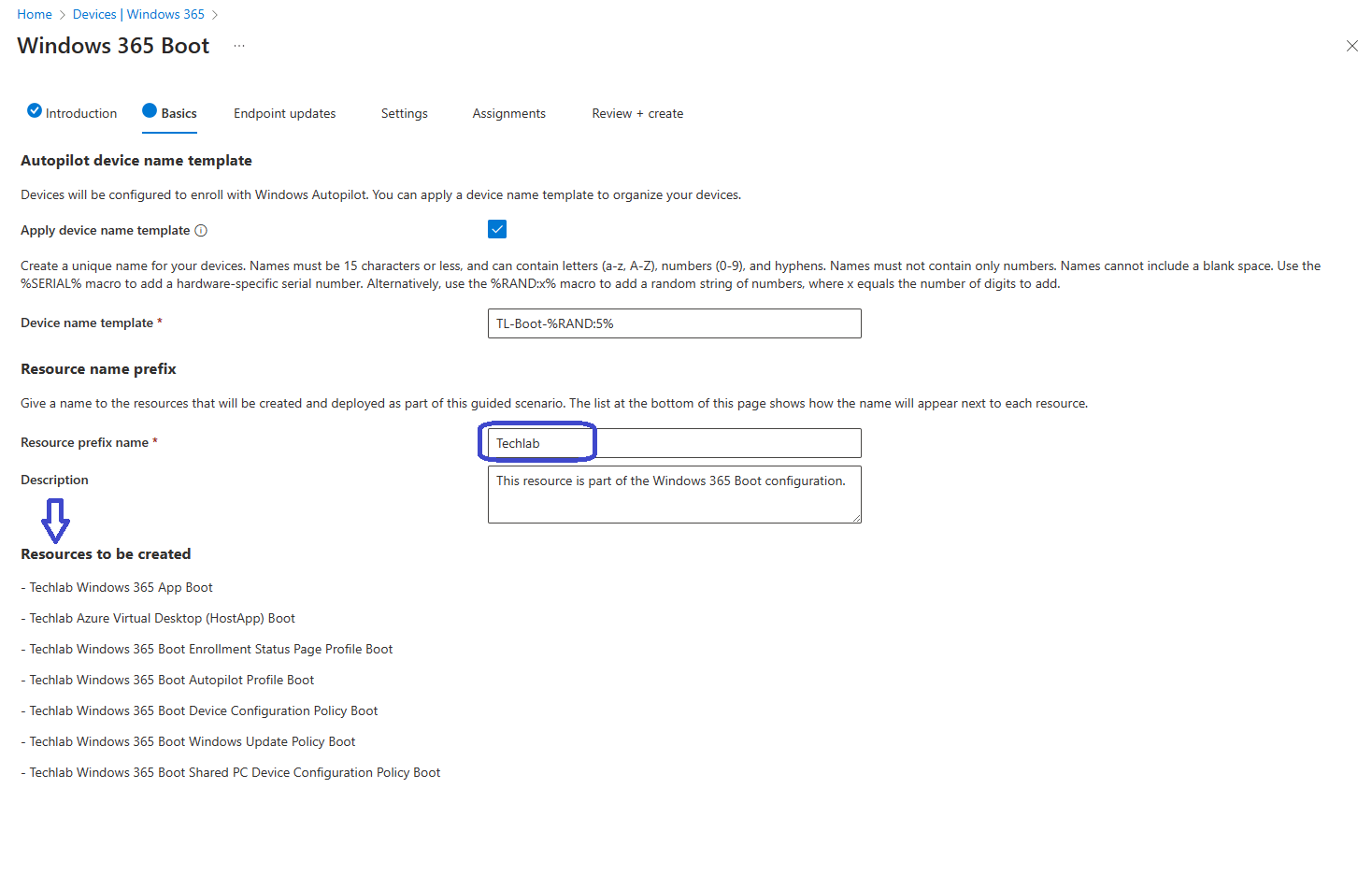
In the Basics tab we can provide a name for the endpoints that will be configured as a Windows 365 Boot device and we can define a prefix. This prefix will be used for each resource that this guide will create and you can actually have a preview in the Resources to be created section.
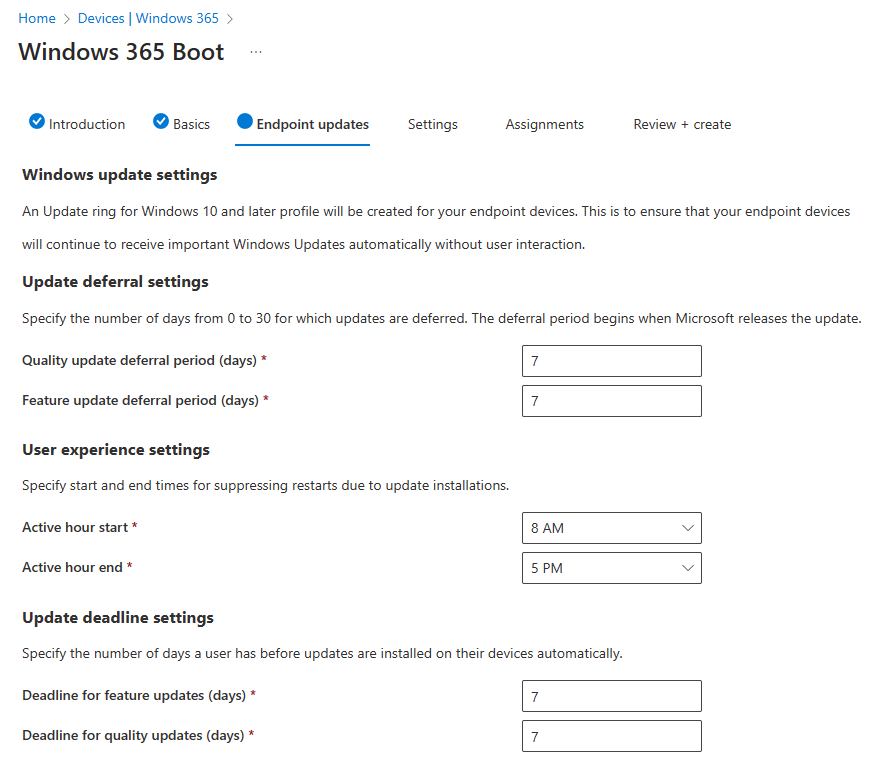
The next step is all about Endpoint updates. The defaults are OK for this demo so I’ll just use them.
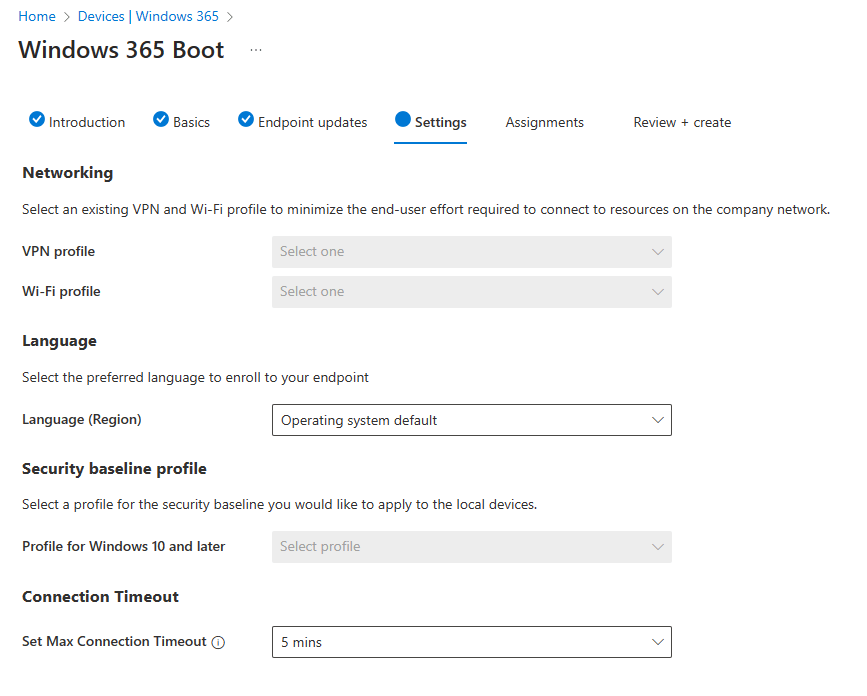
In the Settings tab we can configure some networking details like a VPN profile or a WiFi profile (if you have them available).
You can specify which language you want to use on the endpoint and apply a security baseline if you have one configured.
And you can finish up by specifying a timeout after a user signs into a Cloud PC. The default (and recommended setting) is 5 minutes and that works for me.
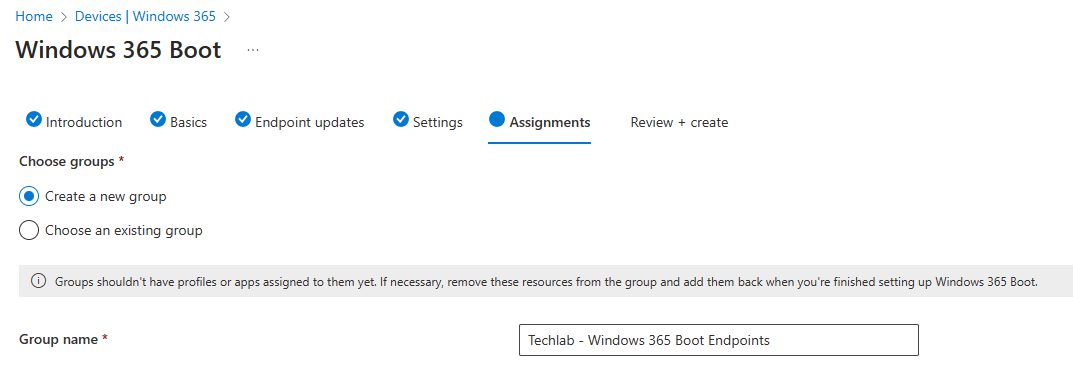
In the Assignments tab we can assign a group to these resources. After carefully reading the warning on screen, I’ve decided to grab a coffee and create a new group.
As always we finish up with a review + create tab. It’s a great moment to admire your awesome work, enjoy the coffee you got yourself and preview the settings you want. In this case I recommend to doublecheck the names of the resources that are about to be created.
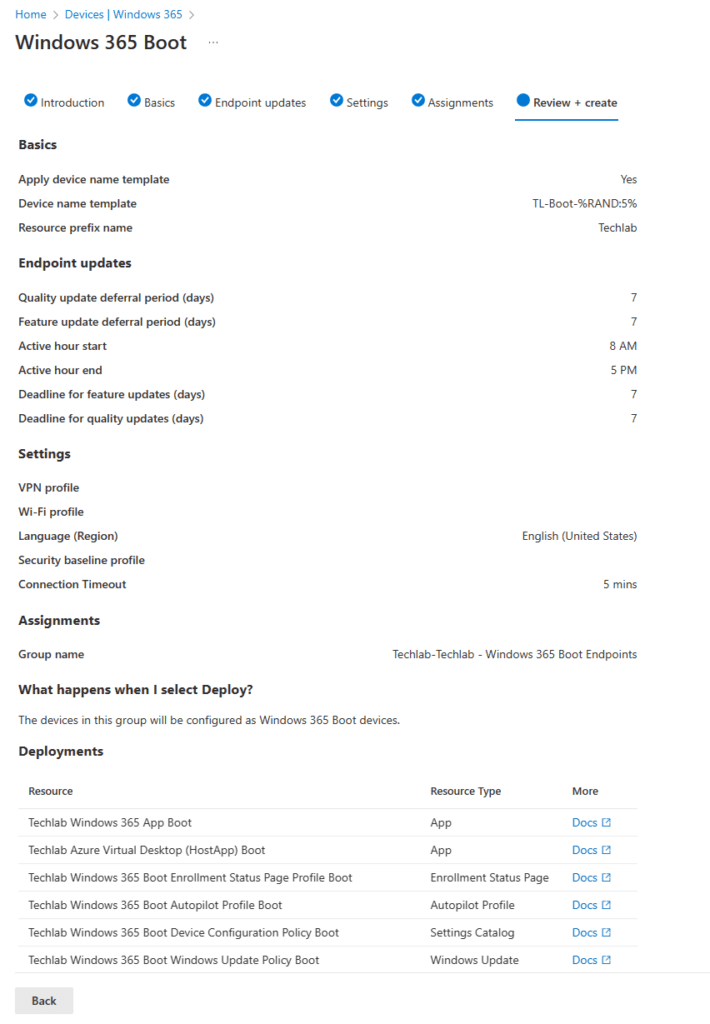
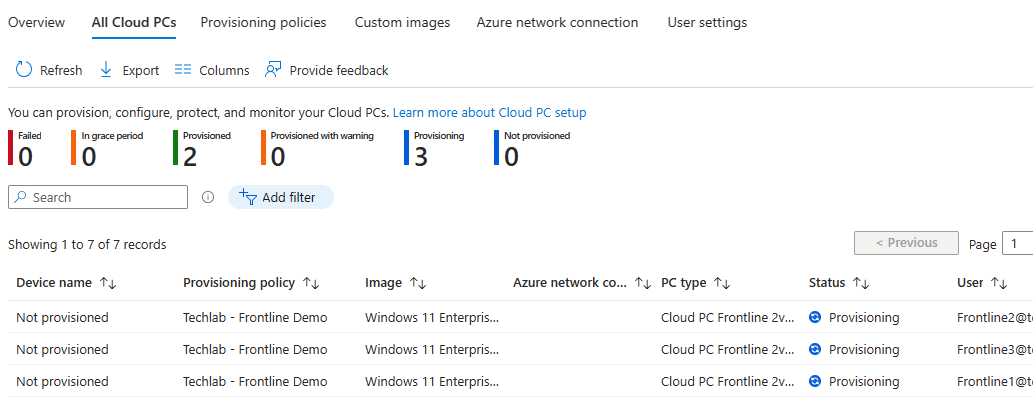
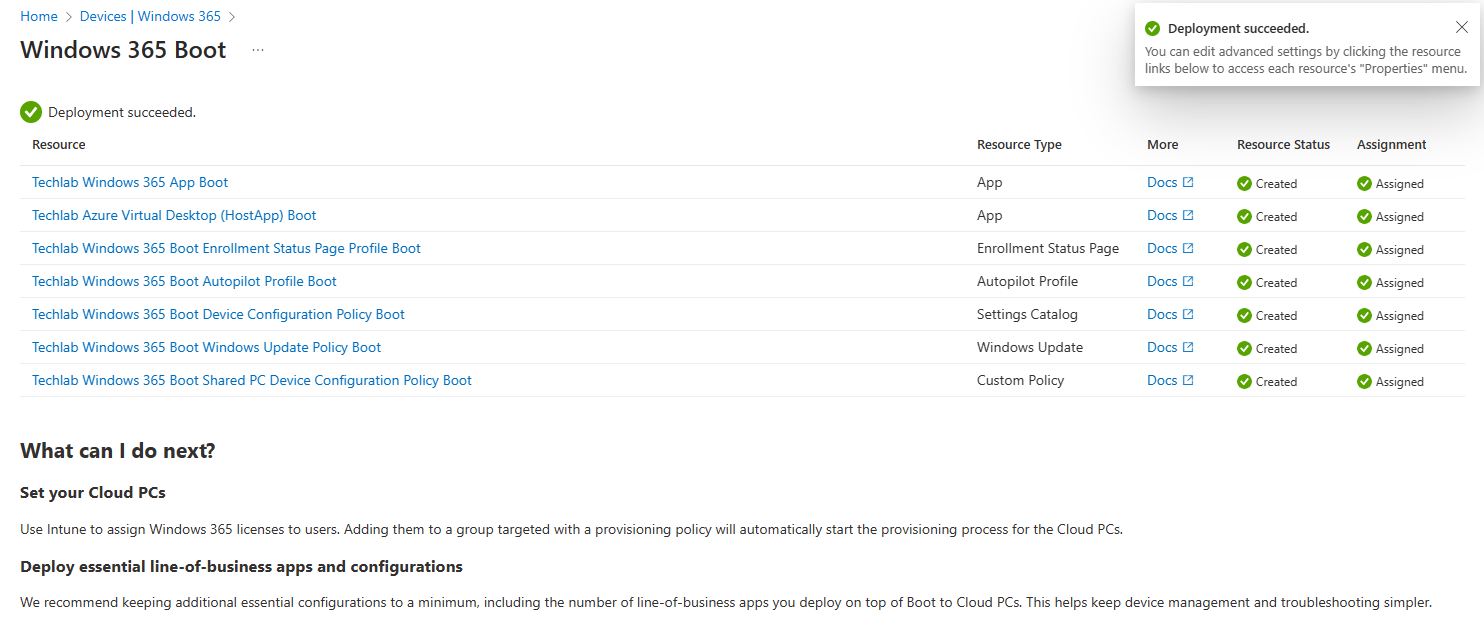
You will get a nice overview of the deployment in Microsoft Intune once you click save:
And that concludes the Windows 365 Boot guide! Well done Microsoft! So what’s next?
Make sure to deploy an endpoint as a Windows 365 Boot device and make sure to keep to the bare minimum configuration for the Boot enabled endpoints.
Once that is done, we can move on to…
Demoing Windows 365 Frontline on a Windows 365 Boot Endpoint
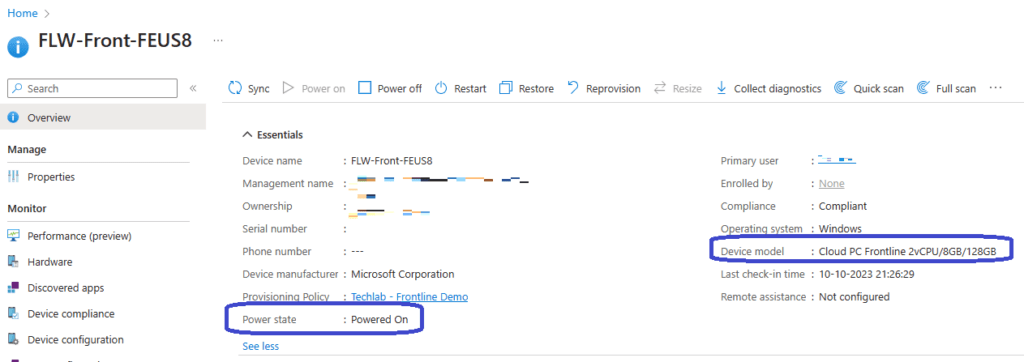
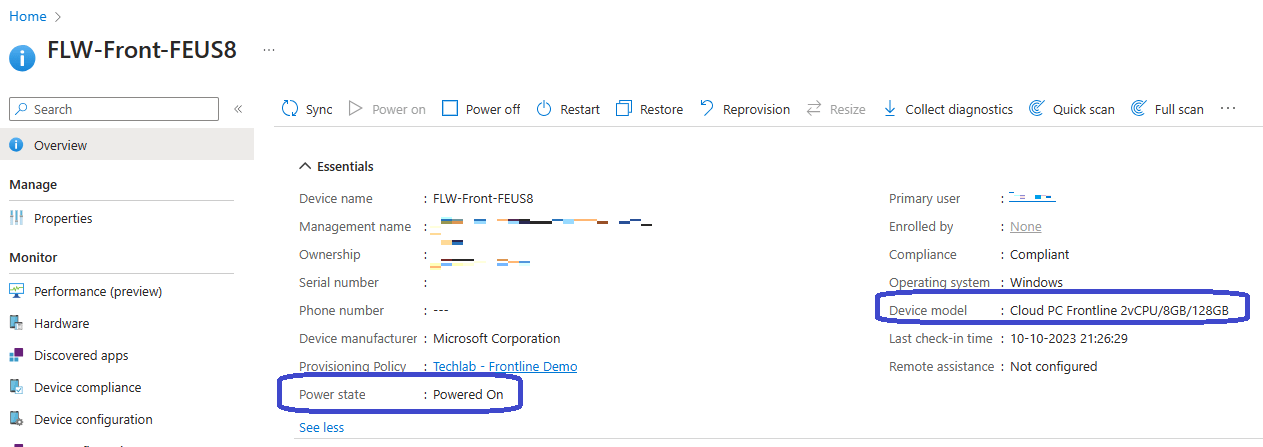
At this point I’ve deployed my Frontline Cloud PCs which are turned off and I’ve created a new VM. Installed Windows 11 and uploaded the hash and installed it using Windows Autopilot. All there is left to do is to sign in to the newly created Windows 365 Boot endpoint using my Frontline license and see if that works. Here goes;
A quick check in Microsoft Intune shows that the Power state is now set to Powered On.
Resources
I used the following resources for this post:

2 thoughts on “Combining Windows 365 Boot and Frontline”