What’s up, everyone!
Time flies when you are having fun! It’s already back in February when I wrote a post on how to use a FIDO2 security key to sign into a Cloud PC. I had great response regarding this post (thanks for that!). Since then I had a chat with my friends at Yubico and they have been awesome and provided me with a YubiKey 5C and even better, a YubiKey 5C NFC. This week I will put the 5C with NFC capabilities to good use in this post which is all about signing into a Cloud PC from a Windows 365 Boot endpoint in shared device mode. (Learn more about Windows 365 Boot Shared Device Mode here).
What if users just have to tap their NFC security key to their Windows 365 Boot endpoint, enter their personal PIN and gain access to their personal Cloud PC? Sounds too good to be true or reality? Find out all about it in this post.
Enjoy!
Prerequisites
Here are some prerequisites if you want to follow along:
- A Windows 365 Boot endpoint in shared device mode.
- An endpoint with NFC or an NFC reader. I used the ACS ACR122U model.
- A security key with NFC capabilities. I used the YubiKey 5C NFC. (link)
Part 1: Prepare the environment
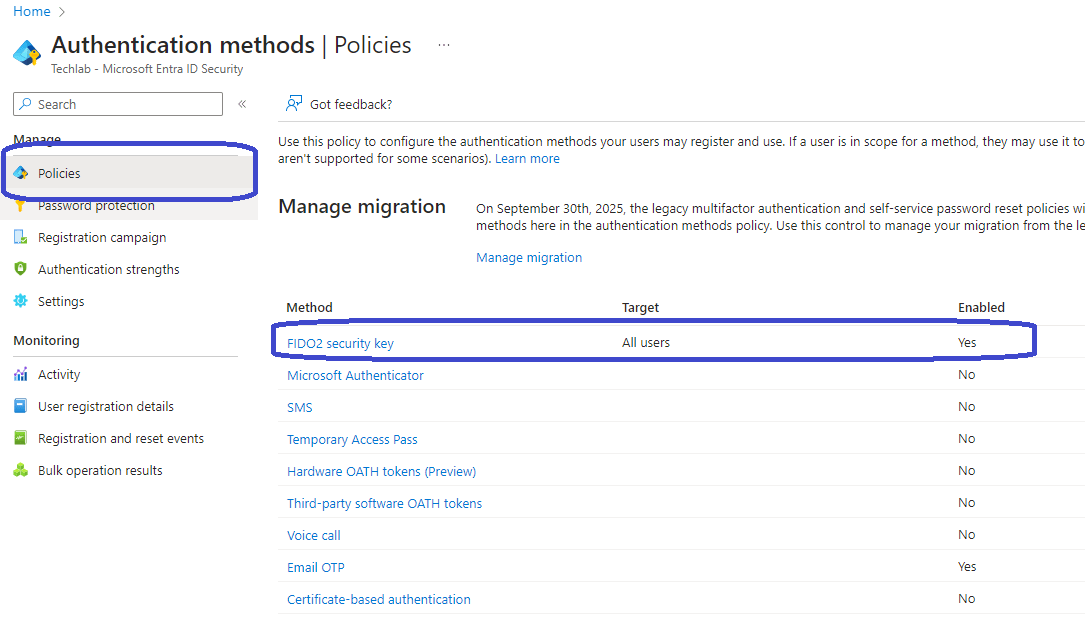
The first thing on our to do list is to make sure that FIDO2 is an allowed authentication method. Go to the Entra portal, Protection, Authentication methods.
Bad example, right! It’s already configured in my environment. No worries, enabling it is easy to do. Click FIDO2 security key and switch the slider to Enable. By default this setting applies to all users buy you can go more granular by configuring an Entra ID group.
Th second step in our to do list is to make sure that security keys are allowed to sign in to Windows. There are two places where you validate this setting:
1: Tenant wide
2: Configuration policy
Tenant wide
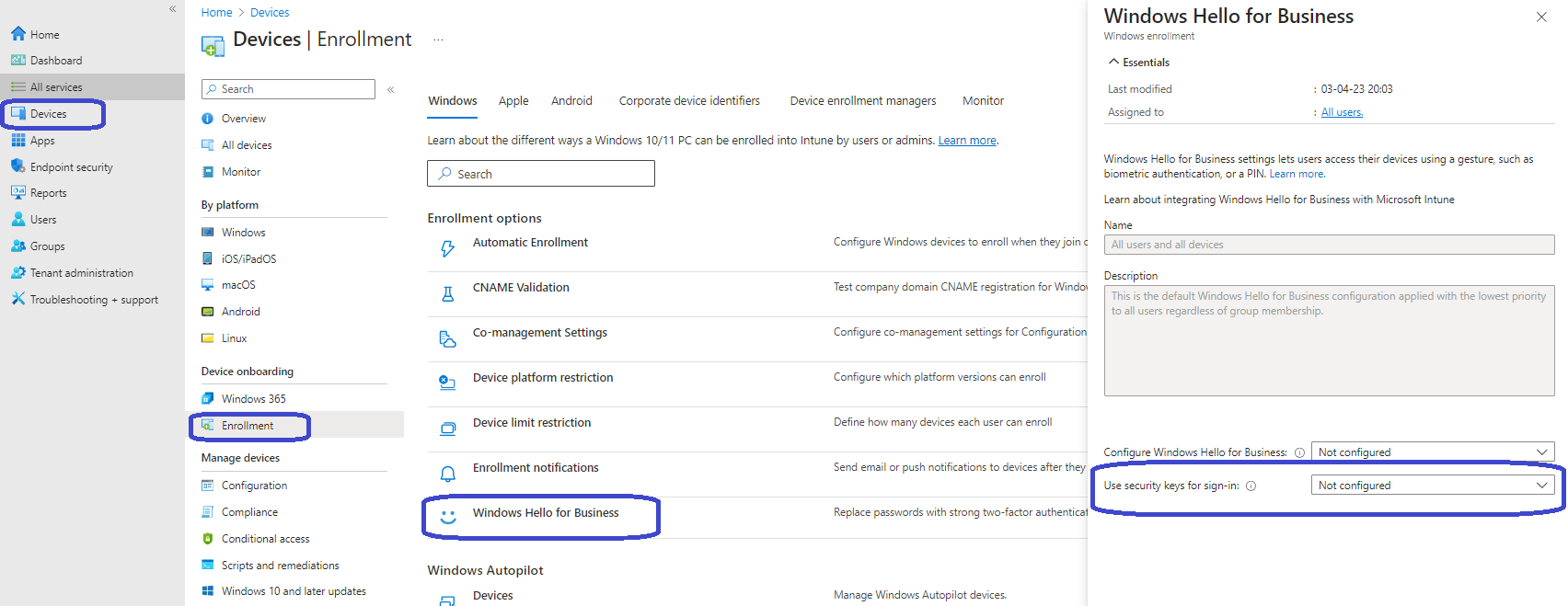
From the Microsoft Intune admin center, Devices, Enrollment, Windows Hello for Business. Locate the Use security keys for sign-in setting. Make sure it’s not set to Disabled.
Configuration policy
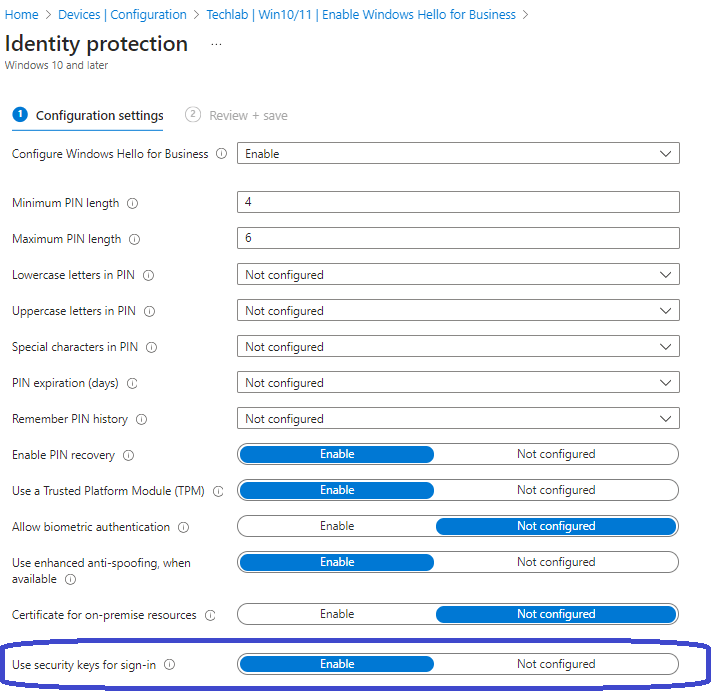
From the Microsoft Intune admin center, Devices, Configuration and select the configuration policy that you’ve used to configure Windows Hello for Business and that targets the desired endpoints. The following screenshot shows my demo configuration:
Make sure to Enable the Use security keys for sign-in setting and save the configuration.
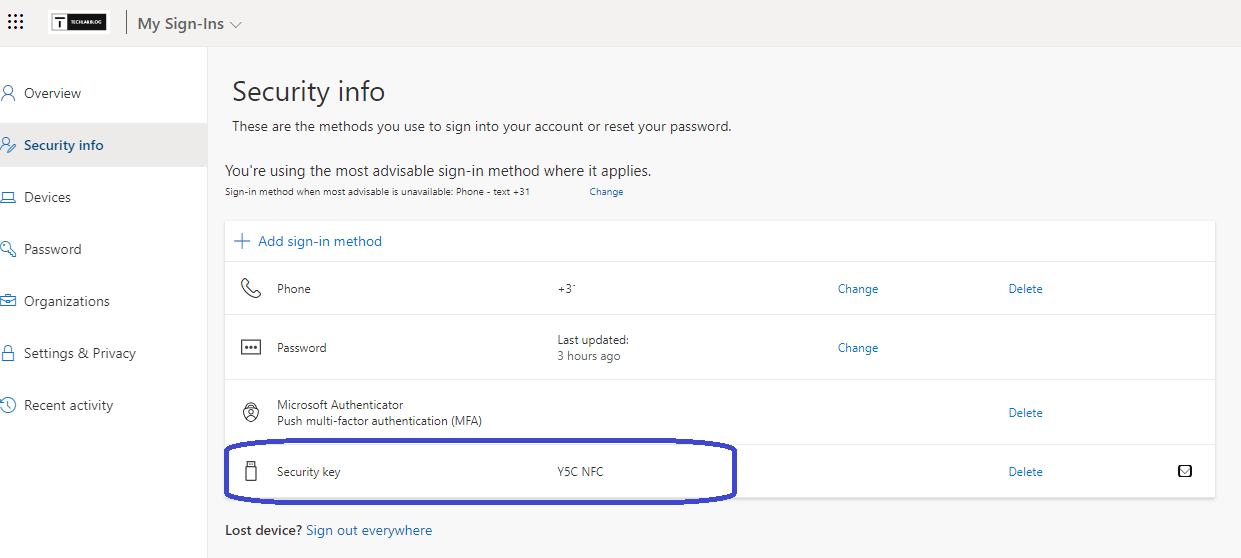
We arrived at the final preparation step as we need to configure the security key for the user. You can either use Windows for this task if the user is signed into Windows. In this case, go to Settings, Account, Sign-in options, Security key.
Alternatively you can use https://aka.ms/mysignins and sign in with the account where you want to add the security key. This can be done from your own device or an unmanaged device like your personal laptop. Should you use your personal laptop; do not use Edge in the inprivate mode, doing so will fail.
Use the + Add sign-in method button in the ribbon. You can either use:
- USB: connect and configure your security using USB
- NFC: configure the security key via NFC (Tap/PIN/Tap)
You should end up with something like this:
We have now successfully configured the prerequisites for Entra ID, Windows Hello for Business and configured the NFC security key for the user.
Part 2: The user experience of signing in using an NFC security key
So what does the user experience look like? Users sign in using the following steps:
Let’s find out in the next video:
- Power up the device and wait until you see the lock screen.
- Tap the security key on the reader.
- Provide the PIN.
- Watch the magic happen!
Here’s a video of the user experience:
There you go! It’s as simple as that to use a Windows 365 Boot device as a shared device and have users sign in password-less using a security key with NFC.
Personal findings
I worked with FIDO2 USB security keys before, but I didn’t have experience with NFC security keys yet. And even though it seems pretty straightforward, there are a couple of things I want to share with you and perhaps save you some time.
- “The tap”. The correct procedure is tap/PIN/tap. This did not work in my case. If you experience the same issue, you should replace the word “tap” with “just put your NFC key on the reader pad and do not touch it!” The more you fiddle, the more it will fight you and it will throw many unnecessary errors. Notice that I placed the security key on the NFC reader pad and just left it there until the sign-in process completed successfully.
- Did I mention that you shouldn’t hold your NFC in your fingers? By holding your NFC key in your fingers, you probably will hold the key at an angle to the pad and that distance might disrupt reading the security key.
- Make sure you have good hardware. Vendors like Yubico can assist you in choosing the correct security key and in case you are going for a NFC version, they can advise you if that model is tested and supported. Why a special mention for this? I did not have any issues with configuring the YubiKey or setting up Windows 365 Boot / Entra etc. I had the most issues with the reader. When I plugged it into my laptop, it didn’t connect properly. I noticed much better performance when I plugged my Microsoft Travel Hub into my laptop and connected the NFC reader into the travel hub.
- Are you getting multiple questions to tap the security key to the NFC pad? You probably will find your solution in the advice above!